Hot topics Regarding IOT in 2024
In 2014, the Internet of Things (IoT) gained significant attention as an emerging technology with the potential to transform industries and daily life. Key hot topics included the vast expansion of connected devices, with estimates predicting billions of new smart gadgets coming online, thereby increasing the need for robust data management and security protocols.
Justin Lee
In 2014, the Internet of Things (IoT) gained significant attention as an emerging technology with the potential to transform industries and daily life. Key hot topics included the vast expansion of connected devices, with estimates predicting billions of new smart gadgets coming online, thereby increasing the need for robust data management and security protocols. The integration of artificial intelligence and the Internet of Things brought about by the rapid development of AI and other technologies; Discussions centered on interoperability challenges between devices and platforms, as diverse manufacturers began to compete for market share. Additionally, the emergence of smart cities highlighted the potential for IoT in urban planning, traffic management, and public safety. Privacy concerns also became a focal point, as consumers grew wary of the data being collected by their connected devices, prompting calls for more transparent policies and regulations.
Rapid rise of connected devices
The IoT industry experienced significant and notable growth in the year 2024, largely fueled by the rapid rise of connected devices permeating both daily life and various industrial sectors. Billions of innovative devices utilizing advanced communication technologies contributed to the enhancement of smart home solutions, wearable technology, and comprehensive automation systems. This remarkable growth not only improved consumer experiences but also enabled extensive real-time data collection and thorough analysis, resulting in better operational efficiency and more informed decision-making processes. However, the increasing adoption of these interconnected devices raised important cybersecurity and data privacy concerns, which in turn led to essential advancements in protective measures and the development of more rigorous regulations to safeguard users.
The integration of artificial intelligence and the Internet of Things
By cleverly integrating AI algorithms into Internet of Things devices, these devices are like having their own brains, which can directly process and analyze data without the need to transmit data, which greatly reduces the transmission delay and makes the response speed faster! For example, those intelligent security cameras can now analyze surveillance videos in real time, just like detectives, quickly identify any abnormal situation and make security guarding easier.
Moreover, the massive amount of data collected by Internet of Things devices will be transmitted to the cloud platform. There, deep learning and big data analysis, two super powerful "brains", will carefully process and analyze them, just like a super smart magician, turning these data into valuable information and knowledge to achieve more intelligent management!
Especially in the field of intelligent manufacturing, cloud AI is like a super commander, which can optimize the production process and make the whole production process smoother and more efficient. It can also predict the maintenance needs of the equipment, just like a thoughtful little assistant, telling us in advance that the equipment may need maintenance or repair, so as to avoid affecting the production progress due to equipment failure!
Discussions centered on interoperability challenges
Discussions in 2024 regarding interoperability challenges within the IoT industry highlight the ongoing struggle to create seamless integration among diverse devices and platforms. As the number of connected devices continues to grow, stakeholders face significant obstacles related to varying communication protocols, data formats, and security standards. These challenges hinder effective data exchange and collaboration between IoT systems, leading to inefficiencies and increased operational costs. Industry leaders emphasize the importance of developing standardized frameworks and protocols that can accommodate the varied ecosystems while ensuring data privacy and security. Collaborative efforts among manufacturers, software developers, and regulatory bodies are critical to overcoming these interoperability issues and unlocking the full potential of IoT solutions.
the emergence of smart cities highlighted the potential for IoT in urban planning
The emergence of smart cities in 2024 highlights the transformative potential of the Internet of Things (IoT) in urban planning. As municipalities increasingly integrate IoT technologies, they create interconnected systems that enhance urban living by improving efficiency, sustainability, and public services. Smart sensors and devices, embedded in infrastructure, allow for real-time data collection on traffic patterns, energy usage, and resource management, enabling city planners to make informed decisions that respond to the dynamic needs of residents. This integration not only promotes environmental stewardship through optimized resource consumption but also fosters economic growth by attracting tech-savvy businesses and enhancing the overall quality of life for citizens. As cities continue to evolve, the role of IoT in shaping resilient, responsive urban environments becomes increasingly critical.
consumers growing wary of the data
In 2024, consumers are increasingly wary of the vast amounts of data being collected by their connected devices, raising significant concerns about privacy and security. As smart technology becomes more integrated into daily life, individuals are demanding greater transparency regarding how their information is utilized and shared. This growing unease has prompted calls for more stringent policies and regulations governing data collection practices in the Internet of Things (IoT) sector. Consumers seek assurances that their personal data will be safeguarded and used ethically, pushing policymakers to establish clearer guidelines that prioritize user consent and accountability in data management.
Justin's Shared Docs is a platform presenting Justin Duman Lee's public files, primarily focused on professional topics such as strategy, management, and marketing within the sectors of industrial estates, IoT, and life sciences. In addition to work-related documents, the collection includes personal narratives, offering insights into both his professional expertise and personal experiences.
The latest updates in unmanned driving
近年来,无人驾驶技术取得了重大进展,带动了该领域的许多有前景的发展。以下是无人驾驶领域的一些最激动人心的更新
Justin D. Lee
Unmanned driving, commonly referred to as autonomous driving, has been a topic of great interest in recent times due to its potential to transform the automotive industry and the way we travel. Self-driving cars, trucks, and other vehicles are attracting huge sums of investment from governments and corporations alike, with the promise of making travel more efficient, safe, and comfortable.
Unmanned driving technology has made significant progress in recent years, leading to many promising developments in the field. Here are some of the most exciting updates in unmanned driving:
1. Increased Investment: The market for autonomous driving technologies has been growing rapidly, with huge investments being poured into the development of new technologies. According to a recent report by Allied Market Research, the global autonomous vehicle market is expected to reach $556.67 Billion by 2026, growing at a CAGR of 39.47% from 2019 to 2026.
2. Advancements in Machine Learning and AI: Machine learning and AI are essential to unmanned driving technology, and advancements in these fields have accelerated the development of autonomous vehicles. These technologies have enabled self-driving cars to learn from their surroundings and make decisions in real-time.
3. Regulations and Standards: Many countries are now introducing regulations and standards for autonomous driving, which has helped to establish safety protocols and promote the development of new technologies. Some of the most notable regulatory bodies include the National Highway Traffic Safety Administration (NHTSA) in the US, the European Union Agency for Railways (ERA), and the International Organization for Standardization (ISO).
4. Commercial Applications: Autonomous vehicles are increasingly being used for commercial purposes, including delivery services and public transportation. For example, in 2019, Waymo launched a self-driving taxi service in Phoenix, Arizona, which has transported tens of thousands of passengers to date.
5. Technological Partnerships: Many tech companies and auto manufacturers are partnering to work on autonomous driving technologies. For instance, Aurora, a startup focused on developing self-driving vehicle technology, has partnered with companies such as Fiat Chrysler, Hyundai, and Uber.
Unmanned driving is an exciting and rapidly evolving field that holds much promise for the future of transportation. The latest updates in unmanned driving, including increased investment, advancements in machine learning and AI, regulatory standards, commercial applications, and technological partnerships, all point towards a more autonomous driving future. As we continue to make progress in these areas, the benefits of unmanned driving, such as improved safety and efficiency, will become more and more apparent.
Establishing Grades for Pharmaceutical RFID Tag Performance
RAIN Alliance
If you follow market trends, there is serious momentum towards the implementation of RAIN RFID (UHF RFID) in healthcare and pharmaceutical applications. Current applications of RAIN RFID in healthcare include asset tracking (beds, IV pumps, etc.), inventory management, and dispensing of medical devices, medication, and surgical supplies. In the case of pharmaceutical items, the tagging has been accomplished at the hospital facility, as opposed to being tagged at the source of manufacture. However, last year, a global pharmaceutical manufacturer began tagging anesthesia medication at the source of manufacture, starting a trend that will revolutionize the medication supply chain.
As more pharmaceutical companies begin tagging their medications, we must establish a tagged item performance grading system, to ensure that RAIN RFID tagged medications are accurately identified across all applications in this complex supply chain. During the adoption and growth of RFID tagging in the apparel industry end-users sought tagged item performance grades they could follow to help de-risk investments in RAIN technology.
RAIN retail apparel applications, based on standards outlined by the ARC RFID Lab at Auburn University and GS1, are primarily free space inventory solutions involving textile materials. Solutions for pharmaceutical items, however, involve a complex spectrum of form factors, materials, ingredients, and configurations, which are stored in enclosures ranging from small drawers to large refrigerators. Therefore, any tagged medication grading system must include a correlation of the grades to specific applications. For this reason, the Axia Institute is recommending the use of the GS1 Tagged-Item Performance Protocol (TIPP) methodology.
The Tagged-Item Performance Protocol (TIPP) methodology was developed by GS1, a neutral, not-for-profit organization that develops and maintains the standards for the most widely used supply chain systems in the world. The main benefit of the GS1 TIPP standard is that the testing is performed on the actual product and in real-world applications. Testing tagged items is essential because the medications, packaging (syringes, vials, IV bags, etc.), and product orientation can affect overall RF performance.
The GS1 TIPP framework allows for the submission of new grades and is led by a global standards organization of which most pharmaceutical manufacturers are already members. Third-party testing companies and RAIN RFID labs can closely collaborate with tag manufactures, medication automation system providers, and pharmaceutical manufacturers to define the specific requirements of their products for specific applications within the hospitals. The proposed pharmaceutical family grades will open an advanced globally accessible avenue for all the active nodes of the supply chain to implement and validate RFID tags for target pharmaceutical applications. This will facilitate the adoption of pharmaceutical RFID tagging around the globe, leading to the implementation of RAIN solutions that deter counterfeiting and diversion, while increasing patient safety and improving patient care.
The ARC RFID Lab has developed the ARC “Specification S” that could partially mimic pharmaceutical industry requirements. Although the test is robust, it relies substantially on testing the RF performance of a tag while the tag is on paper or cardstock and includes some minimal on-product testing. This testing does not fully account for the orientation of the product, the unique dielectrics of glass vials/syringes, nor the actual medications. Specification S is a single tag test, and it does not address the impact of multiple samples adjacent to each other in a small environment, something that occurs in smart cabinets at the hospitals. Moreover, this test was designed for the apparel industry with the flexibility of using large inlays with long read distances. Overall, Spec S could not reflect the actual requirement of a custom size inlay designed for a narrow 1mL syringe which should be readable at different orientations in a short read range shelf surrounded by multiple tagged items. Not addressing these essential factors in RF testing could lead to failure of RAIN solutions to provide accurate data critical to patient care and safety.
The RAIN Alliance Healthcare Workgroup is proposing an open and interoperable tagged medication grading system, administered by GS1, in which entities can propose grades, participate in the creation of grades, and benchmark against established grades, as opposed to relying on one entity to manage the entire process.
IOT TRENDS AND PREDICTIONS TO LOOK OUT FOR IN 2023
IOT Latest News
The Internet of Things (IoT) describes the network of physical objects things that are embedded with sensors, software, and other technologies to connect and exchange data with other devices and systems over the internet. IoT’s ability to enable devices and equipment to communicate will impact lives. The IoT will continue to deliver new opportunities for digital business innovation for the next decade, many of which will be enabled by new or improved technologies. Take a look at the following IoT trends and predictions that are happening now.
Solutions for Sustainable Energy: Renewable energy was the only energy source that saw increasing consumption throughout the epidemic. Breakthroughs in sustainable energy solutions, when combined with the improved practicality of energy sources like liquid hydrogen, and biofuels, are sure to have far-reaching environmental consequences.
Artificial Intelligence: Data is the fuel that powers the Internet of Things and the organization’s ability to derive meaning from it will define its long-term success. AI will be applied to a wide range of IoT information, including video, still images, speech, network traffic activity, and sensor data. It will be possible to achieve good results with AI in a wide range of IoT situations.
Healthcare Spearheads IoT Adoption: The healthcare industry has been tinkering with Internet of Things technology for years now. IoT will make smart buildings out of healthcare facilities, drive revenue, and help healthcare providers save on costs. IoT adoption has become even more crucial to the healthcare industry during the pandemic.
Infonomics and Data Broking: IoT projects showed that 35 percent of respondents were selling or planning to sell data collected by their products and services. By 2023, the buying and selling of IoT data will become an essential part of many IoT systems.
The Emergence of Smart Cities: IoT adoption will result in the establishment of smart cities. Smart cities do not only focus on making life comfortable for people. These cities improve the social, environmental, and financial aspects of urban living. Smart cities will become a key ingredient in improving sustainability and quality of living.
Cyber Security Mesh: Cyber Security Mesh provides a comprehensive approach to tackling security flaws and gaps connected with end-users and devices situated beyond network perimeters. It employs a distributed structure rather than constructing a perimeter based on the reach of a network.
Hyper Automation: Hyper Automation is a critical tool for firms that want to be future-proof. The future of IoT work with hyper-automation involves performing tasks with robots rather than humans, a re-imagining of work as accomplished by technologically empowered workers.
Powering Smart Stores: IoT can also record how visitors spend their time on the store premises. Using data collected by such systems, store owners can make the needed improvements to their inventory and even the way products are displayed on their shelves.
Intelligent Work-from-Home Technologies: Work-from-home technology has become critical to the post-pandemic era’s ever-increasing speed of IoT trends. Most Internet of Things trends has lately seen exponential growth. Furthermore, investors and analysts seek for these creative remote working rules to assess a company’s adaptability.
IoT Governance: As the IoT continues to expand, the need for a governance framework that ensures appropriate behavior in the creation, use, and deletion of information related to the Internet of Things projects will become increasingly important. Governance ranges from simple technical tasks such as device audits and firmware updates to more complex issues.
Disclaimer: The information provided in this article is solely the author’s opinion and not investment advice – it is provided for educational purposes only. By using this, you agree that the information does not constitute any investment or financial instructions. Do conduct your own research and reach out to financial advisors before making any investment decisions.
Chipotle Tests RFID Technology for Traceability
NEWPORT BEACH, Calif.
Chipotle Mexican Grill announced it is testing radio-frequency identification (RFID) technology to enhance its traceability and inventory systems at its Chicago distribution center and approximately 200 restaurants in the greater Chicago area. Chipotle is one of the first major restaurant companies to leverage RFID case labels to track ingredients from suppliers to restaurants via serialization.
"RFID labels transform inventory management into an automatic, digital function that optimizes restaurant operations and gives our Restaurant Support Centers access to inventory data in real-time," said Scott Boatwright, chief restaurant officer. "This integrated technology is improving our employee experience in participating restaurants while also benefiting our supply partners."
Chipotle said it has purchased more than 35 million pounds of locally grown produce in 2021 and has spent more than $400 million in food premiums over the last two years to buy responsibly sourced and humanely raised ingredients. The brand is giving further transparency into the direct source of its ingredients. The company has worked closely with the Auburn University RFID Lab to refine the pilot program, which is being tested on meat, dairy and avocados from five Chipotle suppliers. Ingredients in the test arrive at Chipotle restaurants affixed with RFID enabled case labels and are scanned by RFID readers, which complement existing scanners in the restaurants, requiring minimal incremental investment. The tech-enabled traceability system is designed to allow the company to act on food safety and quality concerns swiftly, efficiently and precisely, it claimed.
Participating suppliers have invested in RFID technology using Chipotle specifications, which is anticipated to save suppliers time on inventory management and stock rotation, mitigate human error and increase expiration date visibility and accountability. Chipotle invited key supply partners to participate in the test and provided partners with an RFID playbook with best practices and benefits of the program. The brand is leveraging its stage-gate process to test, listen and learn from employees and suppliers before deciding on a system-wide rollout of RFID labels.
"We have been developing our RFID program for two years and see this innovation as the next evolution of traceability and food safety," said Laurie Schalow, chief corporate affairs and food safety officer. "We are excited to test this innovation in the field with our suppliers and restaurants to enhance our robust traceability program."
Chipotle teamed up with industry-leading RFID partners including RFID software provider Mojix, materials science and RFID innovator Avery Dennison, and RFID reader and encoder solutions provider Zebra Technologies.
Will RFID Help Loosen Amazon’s Grip On Retail?
Amazon can't be happy about Walmart’s decision to dramatically expand the use of RFID in its fleet of stores. Here’s why.
An US giant Amazon employee passes by its logo on the opening day of the new distribution center in Augny, eastern France, on September 23, 2021. (Photo by SEBASTIEN BOZON / AFP) (Photo by SEBASTIEN BOZON/AFP via Getty Images)
AFP VIA GETTY IMAGES
Retailers typically struggle to maintain an accurate view of the precise inventory holdings of each of their stores. This is a huge problem in some merchandise categories, and less so in others. For companies with large store fleets, this has traditionally been treated as a cost of doing business.
Brick and mortar retailers also struggle to effectively manage —- and in some cases even find —- the inventory residing in their stores. This too has been shrugged off as a cost of doing business. And let’s not forget another chronic drain on profit. Theft of store inventory by organized criminals, petty shoplifters, and dishonest employees.
RFID is already helping Walmart fix these issues in several General Merchandise categories (Apparel, Footwear, Sunglasses, Watches, Jewelry) with more now on their way. Elevating inventory accuracy and visibility benefits Walmart’s e-commerce business too, not merely the stores.
Simply put, some longstanding advantages enjoyed by Amazon over Walmart are in the process of being diminished.
What will hurt Amazon even more is if other competitors similarly begin leaning harder on RFID. Or in the case of retailers like Kohl’s, who are quite late to this party, simply begin leaning.
Let’s examine a few of these companies in more detail.
Target
Around 2017 Brian Cornell and the Target team exhibited tremendous foresight (and a high RFIQ) when they decided to begin using RFID in all “soft” Home Goods categories, and not merely use it in Apparel and Footwear.
Target is known to have also begun using RFID on its Heyday brand of Consumer Electronic accessories in recent years, and perhaps on other products too.
It’s fair to say that an expansion of Target’s program into additional categories is long overdue. And it’s possible this expansion is already underway. The obvious questions are this:
1. By January 2023, in which merchandise categories will Walmart be using RFID and Target not?
2. Has Walmart’s category expansion accelerated, or is it likely to accelerate, Target’s plans to use RFID in these categories?
Bed Bath & Beyond
Walmart sells many of the same types of products typically carried by BBBY. But the latter generally carries higher priced merchandise, making Walmart merely an indirect competitor. But the same can’t be said of Target and Macy’s, both of whom have been using RFID for years in many of BBBY’s core categories. Nor can it be said of Nordstrom, Nordstrom Rack, Belk, and Dillard’s, who have begun doing so too.
To what degree will Walmart’s category expansion accelerate the upgrade of BBBY’s “store level” inventory management capabilities?
Best Buy
There is an opportunity here for significant coopetition, defined by Oxford as “collaboration between business competitors, in the hope of mutually beneficial results”. Best Buy and Walmart both stand to gain tremendously if they —- and other retailers with large Consumer Electronics businesses —- step up their coordination with big global brands like Samsung, LG, Sony, and Apple. Industry standards organization GS1 will continue to play an important role facilitating those discussions.
So, it begs the question. Now that Walmart has joined the list of retailers using RFID to manage Wireless and Electronics inventory, will Best Buy’s leadership team elevate Store Level Inventory Accuracy as a strategic priority?
The Bottom Line
The longer it takes retailers to fix the inventory management issues in their stores, the longer Amazon will keep laughing all the way to the bank.
SML Report Shows Retailers Expect Post-Pandemic Growth
BY RICH HANDLEY
Based on input from more than 500 apparel retail decision-makers, the report examines the impacts of COVID-19 on the industry, as well as the current sentiment regarding growth prospects and the challenges in bouncing back.
Dec 03, 2021SML RFID has announced the release of the first half of its two-part "The State of Retail in a Post Pandemic Era" report, which finds that more than a third of retailers feel confident in their ability to grow within the next year, but that recovery from the COVID-19 pandemic remains a concern. The report, which analyzes responses from more than 500 independent senior decision-makers representing apparel retailers in the United States and the United Kingdom, examines the pandemic's impacts on the apparel retail industry, as well as the general sentiment regarding growth prospects and the challenges in bouncing back.
According to SML, the past 18 months have posed a significant challenge for the retail sector due to the coronavirus outbreak. As the report explains, companies were forced to adapt to shifting consumer demands as in-store operations temporarily ground to a halt and as e-commerce became the primary sales channel. Those surveyed for the study deemed recovering from the pandemic to be the most significant obstacle, SML reports, with 38 percent of respondents citing this as their greatest challenge.
Artificial Intelligence and Machine Learning
By Gino Masini, Yin Gao, Sasha Sirotkin
5G brings more stringent requirements for Key Performance Indicators (KPIs) like latency, reliability, user experience, and others; jointly optimizing those KPIs is becoming more challenging due to the increased complexity of foreseen deployments. Operators and vendors are now turning their attention to Artificial Intelligence and Machine Learning (AI/ML) to address this challenge. For this reason, following RAN plenary approval, 3GPP RAN3 has recently started a new Release-17 study on the applications of AI/ML to RAN.
AI can be broadly defined as getting computers to perform tasks regarded as uniquely human. ML is one category of AI techniques: a large and somewhat loosely defined area of computer algorithms able to automatically improve their performance without explicit programming. AI algorithms were first conceived circa 1950, but only in recent years ML has become very popular partly due to massive advancements in computational power and to the possibility to store vast amounts of data. ML techniques have made tremendous progress in fields such as computer vision, natural language processing, and others.
ML algorithms can be divided into the following types:
-Supervised learning: given a training labeled data and desired output, the algorithms produce a function which can be used to predict the output. In other words, supervised learning algorithms infer a generalized rule that maps inputs to outputs. Most Deep Learning approaches are also based on supervised learning.
-Unsupervised learning: given some training data without pre-existing labels, the algorithms can search for patterns to uncover useful information.
-Reinforcement learning (RL): unlike the other types, which include a training phase (typically performed offline) and an inference phase (typically performed in “real time”), this approach is based on “real-time” interaction between an agent and the environment. The agent performs a certain action changing the state of the system, which leads to a “reward” or a “penalty”.
Perhaps the most obvious candidate for AI/ML in RAN is Self-Organizing Networks (SON) functionality, currently part of LTE and NR specifications (it was initially introduced in Rel-8 for LTE). With SON, the network self-adjusts and fine-tunes a range of parameters according to the different radio and traffic conditions, alleviating the burden of manual optimization for the operator. While the algorithms behind SON functions are not standardized in 3GPP, SON implementations are typically rule-based. One of the main differences between SON and an AI-based approach is the switch from a reactive paradigm to a proactive one.
The study has just begun, and at the time of writing we can only provide initial considerations. According to the mandate received from RAN, our study focuses on the functionality and the corresponding types of inputs and outputs (massive data collected from RAN, core network, and terminals), and on potential impacts on existing nodes and interfaces; the detailed AI/ML algorithms are out of RAN3 scope. Within the RAN architecture defined in RAN3, this study prioritizes NG-RAN, including EN-DC. In terms of use cases, the group has agreed to start with energy saving, load balancing, and mobility optimization. Although the importance of avoiding a duplication of SON was recognized, additional use cases may be discussed as the study progresses, according to companies’ contributions. The aim is to define a framework for AI/ML within the current NG-RAN architecture, and the AI/ML workflow being discussed should not prevent “thinking beyond”, if a use case requires so.
Stay tuned for further updates as the study progresses in RAN3, or consider joining us in our journey into the “uncharted” territory of AI/ML in NG-RAN.
Current state of communication systems based on electrical power transmission lines
Antony Ndolo & İsmail Hakkı Çavdar
Journal of Electrical Systems and Information Technology
Abstract
Power line communication technology is a retrofit alternative technology for last mile information technology. Despite several challenges, such as inadequate standards and electromagnetic compatibility, it is maturing. In this review, we have analysed these obstacles and its current application status.
Introduction
Indeed, advancements in communication engineering and technology have brought in revolution in the telecommunication industry. One great impact has been in information and service delivery during the last decades of the twentieth century to date. This is due to the high demand for information created by the huge human population. Better methods and channel models for signal transmission have been researched and developed. For instance, fibre optics has provided waveguide for numerous services at higher speed while inheriting other advantages such immunity to electromagnetic interferences amongst others [1, 2]. Despite all the positive attractions towards fibre communication, it is expensive to install and it is limited to certain areas. That is, remote, rural and mountainous areas. This has necessitated the search for alternative information transmission methods. Power line communication (PLC) is one such alternative.
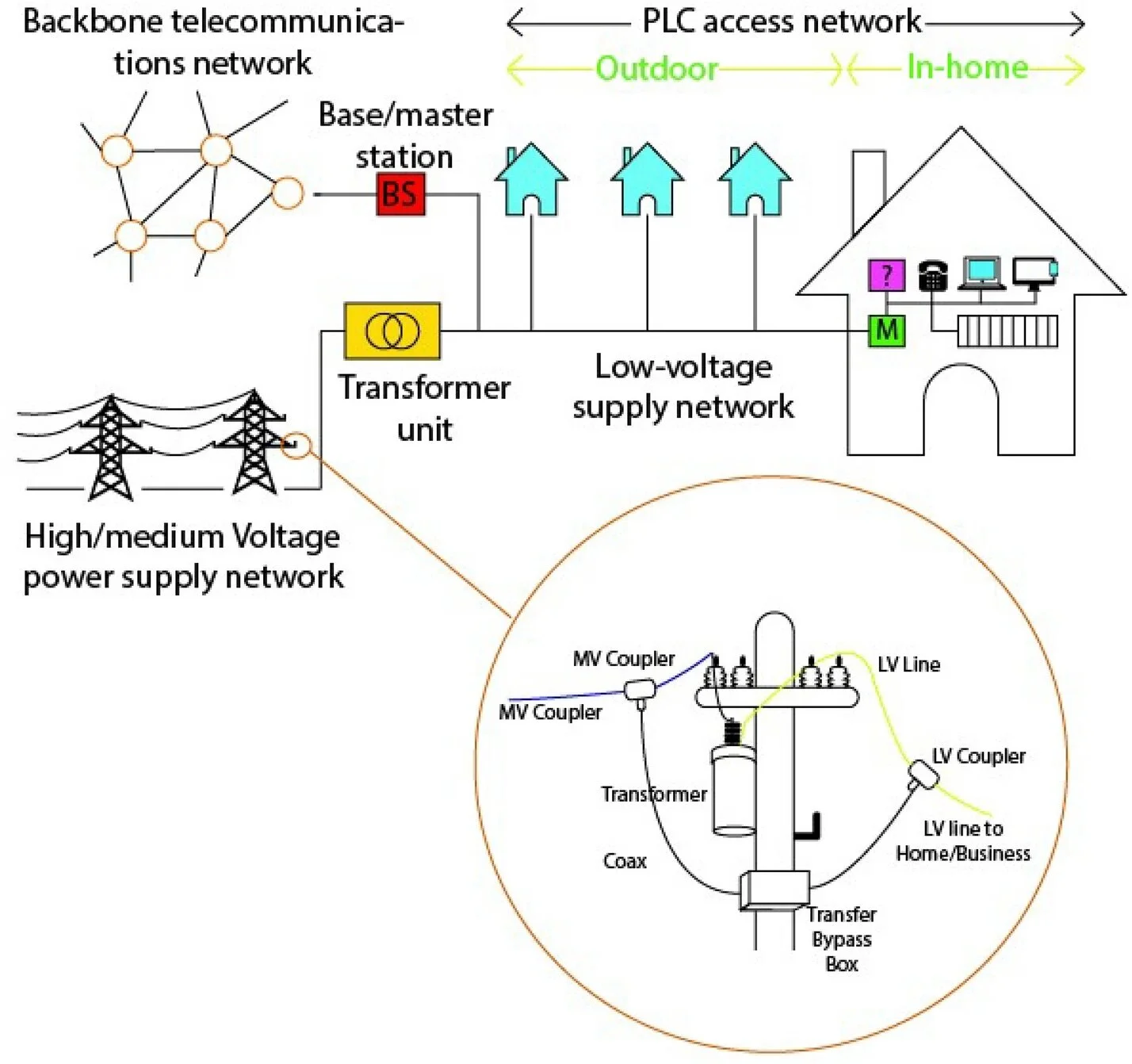
Power line communication technology is the basically a technology that uses pre-existing and installed electrical power cables for transmission of information [3,4,5,6]. Traditionally, such electrical lines were designed exclusively for distribution and transmission of electricity at lower frequency. This frequency varies from country to country, mainly, 50 Hz or 60 Hz. Upon generation of electricity, it is distributed and transmitted through different voltage network. Firstly, electricity is transmitted over high voltage lines, then distribution is done over medium voltage lines, and lastly, it is converted/scaled down using transformers for the end-user consumption in the low-voltage lines. Figure 1 gives summary of PLC structure. This technology is therefore retrofit and economically cheaper compared to other methods. There is no need for new cable installations. Secondly, electrical power network is the most developed, covers large areas and reaches many homesteads. At distribution lines, they are majorly used for the control signals, remote data acquisition and IP telephony services [7].
Structure of power line communication network
Power line communication is divided into three categories, namely ultra-narrowband, narrowband and broadband as summarised in Table 1. The first two are commonly grouped together and termed as narrowband PLC. We will characterise these categories in the next section in details.
Read more
How the IoT Can Help to Distribute COVID-19 Vaccines
BY ROELOF KOOPMANS
The year 2020 brought extraordinary challenges that forced many to overcome and find atypical solutions. As 2021 is being welcomed with open arms, there is a renewed sense of hope and optimism, knowing that governments and pharmaceutical companies are working tirelessly to roll out the COVID-19 vaccines with the intent of safely returning people to everyday life and a sense of normalcy soon.
When it comes to the development, shipping and distribution of the vaccines, there are a few key challenges that pharmaceutical companies, hospitals, logistics service providers and distributors must be mindful of to ensure the vaccines' safe dispersal: tracking shipments to ensure their timely arrival, as well as proper temperature control to make sure they will be safely distributed. The worldwide distribution of the vaccines—in some cases at -70 degrees Celsius (-94 degrees Fahrenheit)—is putting a spotlight on how Internet of Things (IoT)-based sensor technologies can help to enable a challenging supply chain process.
Different use cases in logistics, specifically cold-chain logistics, have unique requirements that need to be independently addressed. In some cases, power must be prioritized, so IoT technology that offers long range and low power consumption qualities may be the right choice. This type of technology also leverages new and better ways to provide geolocation services, which allow cargo, vehicles and other assets to be easily monitored over large geographic regions and within harsh environments.
In scenarios in which long distances may not be traveled, battery life may be a lower priority for a customer, and the user might consider utilizing other types of IoT technologies that are more suitable for their specific use case.IoT technologies can make it easy and affordable for enterprises to track assets throughout supply chains in combination with condition monitoring, which is not limited to temperatures but could also include humidity, shock and other parameters.
COVID-19 vaccine distribution has very much put the spotlight on the importance of temperature control, which must be highly accurate during transit and when the vaccines are stored at healthcare facilities. For example, Moderna's vaccine vials must maintain consistent temperatures and may be stored in refrigerators at between 2 degrees and 8 degrees Celsius (36 degrees and 46 degrees Fahrenheit) for up to 30 days before vials are punctured.
According to a CDC report, Moderna advises that the vaccine vial storage unit temperatures be monitored regularly, and that they be checked and recorded at the beginning of each workday to determine if any excursions have occurred since the last temperature check. Instead of having employees perform manual checks, sensors can do this automatically, alerting staff members if any temperature is about to go out of range.
Additionally, IoT sensors can be placed throughout a healthcare facility to monitor the temperatures of different refrigerators and the vials themselves. The sensors have the ability to periodically measure temperature levels, then send the collected data to a gateway, which forwards that information to a cloud-based application where it will be analyzed. From there, hospital personnel or facility managers would be alerted to any temperature outliers, so that they can be reassured vials are safely stored or take action if necessary.
The use of IoT-enabled sensors can help to ensure the quality of an asset, such as a vaccine, while minimizing the risk of human error. Since such sensors can monitor temperatures in real time, and all of the time, they can help to ensure that vials will not fall out of temperature range. While there is still a way to go before we can safely return to normal, it seems like we're heading in the right direction. IoT technology shows just as much promise, demonstrating to everyone that there are more options for ensuring the safe distribution of the COVID-19 vaccines and other goods globally.
Why Now Is the Time to Invest in Retail Automation for the Future
BY PRAVEEN KANYADI
The retail business is dwindling world over. Even before the pandemic, retailers were dealing with strong competition and declining profit margins. Now, more than a year into lockdown, retailers are striving to learn from past mistakes in a rapidly changing market.
Retail is a massive industry. In the United States, there are approximately 3.8 million retail establishments supporting more than a few trillion dollars in GDP. The industry employs more people than any other sector in the U.S. Therefore, running a retail business in America requires a lot of effort and efficient technology for operation management.
The shift to ecommerce and the COVID-19 outbreak have created a strong market for ecommerce, resulting in the disappearance of several brick-and-mortar retail outlets. A customer setting foot in a retail outlet expects immediate and impeccable service, similar to the one received through an online purchase. Therefore, a retailer should have a well-maintained facility and provide good customer service. This is only possible if technology like workflow automation software is in place.
Removing the Automation Stigma in Retail
Recent research indicates the global retail automation market is expected to be worth more than $19.5 billion by 2024. Retailers are realizing that automation is a mandatory capability to deal with the ongoing crisis rather than a job-killer as once perceived.
For background, workflow automation is a series of automated actions that together form a business process. Since processes are repetitive in nature, workflow automation decreases the need for employees to manually carry out the activities involved in the process. This creates more space and time for staff to focus on higher value activities, in essence reallocating human resources for critical thinking roles like customer service.
Today, workflow automation is no longer just an optional tool for businesses to consider. Process automation is becoming mandatory in all sectors, since it translates to reduced costs and higher levels of productivity. Forward-looking businesses in the retail industry are turning to automation software to streamline operations and improve the bottom line.
The main takeaway from adopting workflow automation software is in eliminating the pain of the mundane, which is why more employees are getting on board. It also reduces the impact of human error that is inevitable in paper-based manual workflows.
Why Do Retailers Need Automation?
The primary impact of workflow automation in retail is in cutting costs and improving operations. This could be realized through better margins, more efficient workflows, higher productivity, time savings, reduced error, better compliance, data collection, and automated inventory checks and updates.
Process automation and workflow automation also help in improving many retail roles. Implementing automation software leads to better planning in marketing and sales. Data collected through these platforms helps retailers analyze and plan their sales strategies better, leading to better lead conversion and customer service. This data also helps businesses strategize their marketing campaigns and create greater brand value in the long run.
Refined Customer Service and Retention
Engaging software to take care of repetitive, mundane tasks frees up time to focus on the most crucial aspect of a retail business—customer service. Healthy and timely customer service is crucial to customer retention and business growth. It also leads to enhanced brand value over time. Giving customers time and attention to take care of their needs and resolve their grievances is very important in creating a strong customer experience.
Workflow and process automation do just that. These systems are able to seamlessly manage customer-related data while creating a space for swift order fulfilment, automated customer support and consistent service each time. In doing so, discrepancies that come with having to interact with a different executive on each visit are prevented.
Reduction of Costs
Automation directly and indirectly leads to cost savings. Going paperless through automation of paper-based processes leads to lowered expenses through reduced use of paper, time and minimal manual error. These types of savings are major factors that lead to significant cost benefits. Retail settings change too swiftly for paper. Searching for documents in the office drawer creates a lag in solving crucial issues like resolving customer complaints.
Using workflow automation software, one can digitize invoices, forms, employee and customer data, inventory and more. This gives retailers centralized access to important information, eliminating paperwork and capturing data straight from the base. This not only helps in cutting costs but also in streamlining retail operations. Process automation software not only ensures that information is collected accurately, but it also makes this data available and accessible at all times. Information located at a centralized source can then be easily extracted, distributed and analyzed when needed.
Ability to Scale
Workflow automation software not only helps increase the sales of a retail business but also in scaling up the enterprise. Manual processes make it really hard to achieve brand growth. Digitized data collection and processes, however, can be scaled up as easily as they are maintained. Imagine inventory that needs to be scaled up but has been manually processed. The mammoth task involved in recording the additional inventory is enough to douse progress.
Apart from the transition to a bigger brand, inventory and sales data from previous years help to analyze in which direction to take your retail business. Data analysis is a crucial process in any business strategy, especially now during a pandemic when consumer behavior is so volatile and unpredictable. Automation tools provide you digital access to this information, helping you make business decisions through a precise and data driven approach.
Goal Setting for Success
Automation can address many challenges facing retailers today; however, successful implementation requires a holistic strategy that aligns to the goals and objectives of a business. A good starting point is to create a vision—identify overarching goals for automation and the processes that could benefit most. Additional investment in people and technology might be needed, depending on the level of automation required. Getting employee and stakeholder buy-in is critical to set automation up for success in the long run. The importance of this step cannot be overstated. Automating processes out of order or focusing on the wrong areas can create risk and minimize results.
There are too many benefits to forgo if choosing to avoiding workflow automation software, and with competition heating up in the market, it is becoming more like a mandatory requirement than an option for retailers today. Rising labor costs, difficulty managing supply chains and increasing expectations from customers are creating an opportunity for automation to assist in developing brand value and creating a firm niche in today's dynamic retail environment.
How to Stop Smart Buildings from Becoming Hackers’ Playgrounds
BY JOHN MEKO
Smart technologies have transformed the way we live, work and communicate—we've become accustomed to a highly tech-enabled lifestyle and we now expect this to be present in our professional lives, too. Such technologies have the ability to make our workspaces more productive with automatic visitor check-in, healthier with improved air quality monitoring, and more sustainable with intelligent energy and water tracking. And when implemented properly, smart technologies enable landlords and building managers to make buildings smarter by using more advanced systems, such as access control, fire alarm and compliance management.
However, security does not end with fire safety and traditional barriers to the outside world. Cyber criminals have become a real threat, invading everything from nanny cameras to refrigerators. Either of those items—and virtually any other Internet of Things (IoT) device—may serve as a conduit to breach an entire network. This is such a concern that, reportedly, President Joe Biden's Peloton will not be allowed to enter the White House for fear of a security breach.
Yet, as people return to their physical workplaces, they'll want to come back to tech-savvy environments. Research shows that 80 percent of employees want to work in a technologically advanced office, so a tech-enabled environment isn't just a nice-to-have for the working world—it's essential. In order to create environments that are safe, secure and free of cyber threats that could compromise users' privacy or their security, landlords need to establish the right protocols and standards in their buildings to empower tenants to have safer environments for their users and their data.
The Smarter the Building, the Larger the Attack Surface
Smart and connected are often used interchangeably, but there is an important differentiator. While any aspect of a building could be "connected"—lights, plumbing, heating and cooling, access control, to name a few—they are not necessarily "smart." A truly smart environment is one which is seamlessly integrated and is purpose-built with security in mind from day one, minimizing the risk of potential threats.
Smart Buildings Must Be Led By the Right Protocols and Standards
Cybersecurity cannot be obtained without first establishing the necessary policies, practices and testing processes that ensure the building's systems and data are secure. Those policies must then be adhered to, in order to ensure that security is maintained. This encompasses not just the approach to securing the networks, but ensuring the users of the building are aware of cyber best practices and regularly follow standard procedures.
These can range from something as simple as ensuring that the computers used for monitoring building-management systems aren't also used for sending emails, or as complex as segmenting networks based on vendor usage. In doing so, landlords can minimize the risks and the potential consequences of a system failure, whether in error or through deliberate action from a malicious hacker outside of the system.
Strong Security Measures Protect Data, Too
Smart buildings contain a treasure trove of data that can be used to learn more about how the space is being used, how much energy is required, and how the space can be customized to better-suit employee needs. Given that every smart asset produces vast amounts of data, organizations need to be able to securely collect, analyze and make smart use of it without compromising security. This means having strong data-governance frameworks and physical protection of the data networks.
The Office of Tomorrow Needs to Be Smarter and More Secure
Smart buildings—those that deliver outstanding outcomes for all users, through digital technology, to exceed their evolving expectations—are expected to provide the highest levels of security. With the right technology at their fingertips, landlords can equip their offices for the modern, tech-loving workforce that has grown accustomed to the benefits of working in a home environment. Using technology as a new incentive to bring the workforce back to the office requires proper thought to go into implementing state-of-the-art technology without compromising on digital or personal safety.
Cyber Threats to Industrial IoT: A Survey on Attacks and Countermeasures
by Konstantinos Tsiknas, Dimitrios Taketzis , Konstantinos Demertzis ,and Charalabos Skianis
Abstract
In today’s Industrial Internet of Things (IIoT) environment, where different systems interact with the physical world, the state proposed by the Industry 4.0 standards can lead to escalating vulnerabilities, especially when these systems receive data streams from multiple intermediaries, requiring multilevel security approaches, in addition to link encryption. At the same time taking into account the heterogeneity of the systems included in the IIoT ecosystem and the non-institutionalized interoperability in terms of hardware and software, serious issues arise as to how to secure these systems. In this framework, given that the protection of industrial equipment is a requirement inextricably linked to technological developments and the use of the IoT, it is important to identify the major vulnerabilities and the associated risks and threats and to suggest the most appropriate countermeasures. In this context, this study provides a description of the attacks against IIoT systems, as well as a thorough analysis of the solutions for these attacks, as they have been proposed in the most recent literature.
1. Introduction
According to the Industry 4.0 standard [1], cyber-physical systems within partially structured smart factories play a central role in monitoring and supervising natural processes by taking autonomous and decentralized decisions in order to maximize the production process. An important factor for achieving this target is the IIoT operational network, where the logical systems communicate and collaborate in real time to implement all kinds of intelligent production solutions, organizational services, and operational processes, required to fulfil the production chain [2].
Specifically, IIoT refers to all interconnected sensors, instruments, and other devices, which in combination with industrial applications, including production and energy management, create a complex network of services, which allows the application of automation at a higher level (see Figure 1) [3].
Figure 1. Generalised IIoT system architecture.
This connectivity allows data collection, exchange, and analysis, as it facilitates the performance improvement across the production chain. It also enables the manufacturing sector to make huge innovative leaps, gain significant extroversion, and develop activities that were previously impossible.
It should be emphasized that the complete transformation of the supply chain into a truly integrated and fully automated process based on the IIoT presupposes the continuous and uninterrupted exchange of information from every stage of the production scale. For the implementation of this communication, IIoT systems are often combined in a multilevel architecture, in which at the hardware level are considered the physical systems (for instance sensors, actuators, control systems, security mechanisms, etc.), at the network level the physical networking media (wired and wireless), and finally at the upper layers the protocols that collect and transmit information from the communications stack.
The continuous increase of connectivity and the use of standard communication protocols, which are implemented under Industry 4.0 standard, however, creates a strong need to protect critical industrial systems from cyber security threats [4]. The industrial systems that control the production process and the operation of the smart factories have constant access to the internet and the industrial networks, but in addition to the information and data of the company to which they belong. Common devices of this type are called industrial control systems (ICS) [5]. The most common ICS are SCADA (supervisory control and data acquisition) systems and sensors used in control loops to collect measurements and provide process automation [6]. These systems are interconnected within the IIoT network; they are active devices in real-time industrial networks, which allow the remote monitoring and control of processes, even when the devices are located in remote areas.
This networking and connectivity improve the operational efficiency of the system, but at the same time, they pose significant challenges for the means of securing the infrastructure [7] in terms of confidentiality, integrity, and availability. Another very important factor that further deteriorates systems’ integrity is that both the machines and the devices in modern industrial facilities are designed initially to facilitate functionality and not to provide a secure environment, which makes them particularly vulnerable to cyber-attacks.
Exploiting the vulnerabilities of the communication protocols that are widely used in the Industrial IoT, as well as the vulnerabilities related to their operational control and how to use them, may result in compromising the critical devices applications, the denial or non-availability of essential services, or even their partial or total destruction, with incalculable consequences [8].
Generally speaking, the most relevant studies conducted so far focus on the security risks in IoT systems. For the particular environment of the Industrial IoT systems, however, there is no available extensive research to our best of our knowledge. In addition, the existing studies fail to contribute substantially to the awareness and clear understanding of the risks associated with IIoT systems as well as the severity of the attacks against them, which in most cases results in great damage and even loss of human lives.
In this sense, this paper presents an extensive study of the most popular ways of attacking industrial applications, as well as the corresponding literature studies related to them, with the aim to provide a more effective, cyber-security-oriented approach and ultimately lead to a more resilient industrial environment.
The main contribution of this work is to provide researchers, but also organizations dealing with Industrial IoT technologies in general, with a comprehensive study on issues related to cyber threats on industrial equipment, as well as the latest countermeasures for the protection of the infrastructure in question, through a critical and benchmarking framework. In this context, the main difference from the other IIoT surveys is the provision of a complete, up to date, and valid reference framework for the identification and the assessment of the risks related to the ever-evolving industrial environment.
The study is organized as follows: Section 2 reviews related work, and Section 3 gives a detailed description of the main risks that can be found in the Industrial IoT environment, the ways they operate, and the associated effective solutions that have been proposed in the most recent literature. Section 4 presents the main results of our study, and finally the last section draws the conclusions and outlines future research directions.
2. Metasurvey
In this section a literature review on the surveys works on the threats associated with the industrial IoT systems. The main security risks are discussed, along with the suggested countermeasures. In particular, we discuss their contribution in the field, and we raise topics of interest that require further investigation and analysis.
Some of the modern attacks on critical infrastructure networks, such as power grids [9], are related to undermining actuators or sensors located in the physical layer, attacks against connections between different devices in the data-link layer, or more specialized attacks to compromise specific control systems such as SCADA devices [10].
SCADA devices are industrial automation control and telemetry systems, consisting of local controllers, which communicate through the industrial IoT network. In cases of advanced cyber-attacks [11], actuators or sensors isolation strategies are usually performed in order to falsify the normal values of the sensors and alter the mode of operation of the cyber-physical systems in an advanced industrial environment. For example, in a cyber-attack on a SCADA potable water disinfection system, the automations related to the treatment and production of clean water, the special flow meters, level, conductivity, and pH analysis, as well as the pumps that calculate the doses of chemicals, could be altered with devastating results for public health.
This study in particular simply lists the building blocks of a functional SCADA architecture, while an analysis of the attacks in the physical layer is completely superficial. In addition, the authors report five types of attacks and attack vectors (source code design and implementation, buffer overflow, SQL injection, cross site scripting (XSS), and effective patch management application), without providing information on the attacks against the software and without giving detailed explanations that could focus on specific methodological approaches on mitigation or prevention. Finally, regarding the communication layer of SCADA systems, the study is devoted to superficial references to the general ways of attacking communication systems and specifically to the unnecessary ports and services, communication channel vulnerabilities, and vulnerabilities of communication protocols. In summary, this study fails to contribute substantially to the awareness and clear understanding of the risks associated with SCADA systems as well as the severity of the attacks against them, which in most cases results in great damage and even loss of human lives.
A more careful approach to the threats related to the industrial IoT systems is presented in [8], where the authors provide a detailed list of possible attacks per layer of the five functional levels of the industrial IoT, with the first three being part of operational technology (OT), while the other two are part of information technology (IT) (see Figure 2). The first functional level includes systems that perform the physical processes of the IIoT, such as embedded devices, sensors, actuators, transmitters, and motors. Attacks aimed at this level require an excellent knowledge of the design of the IIoT system, and access to the specifications of active devices, engineering plans, and detailed information about their installation and operational functionality. The second functional level incorporates the specialized equipment, which communicates and controls the devices of the first level, such as distributed control systems (DCS), programmable logic control (PLCs) and gateways. Attacks at this level aim at preventing legitimate communication between the two levels and controlling the flow of communication. The third functional level is the SCADA and all related industrial automation control and telemetry systems, such as data acquisition devices, master stations, and human machine interfaces, which communicate via the IP protocol. Many of the attacks at the SCADA level rely on IP packet creation techniques with false attributes such as the source address, in order to disguise the identity of the sender of the packet, encouraging the recipient to think that it came from a legitimate network user. The fourth functional level includes business planning services, such as office applications, intranet, web, and mail services. Attacks targeted at this level exploit known or unknown vulnerabilities of these services and enter malicious code where the application expects legitimate data from the user in order to gain access with administrator privileges.
F2. Layered IIoT architecture and possible attacks.
The fifth functional level includes high level services such as analytics, data mining methods handled by the enterprise applications, and cloud computing services. Attacks at this level include a set of malicious actions like interception and deception, but also more advanced types such as adversarial attacks.
It should be noted that the authors of this study, between levels three and four, place a demilitarized zone that includes service servers to which users connect on untrusted networks.
Although this study provides a solid approach on how the IIoT works and the corresponding vulnerabilities associated with it, it is generally considered incomplete, as it does not provide examples of similar attacks, or techniques that could prevent them. It is rather a survey on the known types of attacks, which provides some minimal information that can be easily extracted by the literature.
A holistic approach based on the business planning and the standardization on security requirements designed by the standardization bodies Industrial Consortium and OpenFog Consortium is presented in [12]. Given the complex nature of the IIoT ecosystem, the paper examines the security requirements of industrial connection and communication protocols, based on a three-tier architecture and whether these protocols used at each level provide a certain level of security. In particular, it initially presents an abstract three-tier IIoT architecture, which includes the main components of most IIoT developments, categorizing it in a very clear way (Figure 3).
Figure 3. Three-tier architecture of IIoT connectivity and communications standards.
The edge tier consists of end-points and edge-based gateway devices, composing a proximity network, which connects sensor devices, actuators, and control systems. The gateway devices provide a grouping point for the network, allowing internal inter-level communications, but also layered communications with the higher second level, the platform tier, where the connection is made as an access network for data transfer and control between the levels, which is implemented as connectivity via internet or mobile network. The platform tier contains service-based and middle-ware applications, such as analytics services, data transformation, data integration, etc. The interface with the third and higher level, which is called the enterprise tier, is done with a service network, which is mainly based on the Internet. Finally, the enterprise tier is used for high-level services, such as enterprise applications, cloud computing, domain services, hosting, etc. At this level, end users can interact with the network through specially designed interfaces. Based on this architecture, T. Gebremichael et al. proposed a set of connectivity protocols per level and the security features required for the secure device implementation in IIoT networks. The expansion of these implementation technologies also allows for the distribution of security requirements between the different areas of the network and creates embankments that could serve as backup protection in the event of wide scale breaches.
Finally, the authors of study [13] present a detailed study on SCADA attacks. SCADA systems are the main hardware of the IIoT ecosystem, consist of various entities organized in a hierarchical structure, and are used to monitor the various industrial processes. They include techniques of integration of data acquisition systems, data transmission systems, and human–machine interface (HMI). HMI is a user interface that connects a person to a device, mainly used for data visualization and production time monitoring, while also visualizing machine input and output information. The general description of SCADA architecture includes the master station/terminal unit or master unit (MSU/MTU) which is the control center of a SCADA network, the sub-MSU/sub-MTU acting as a sub-control center, the remote station units/remote terminal units (RSUs/RTUs), acting as the intelligent end devices (IEDs), and the programmable logic controller (PLC), used to monitor or collect data from sensors and actuators. This study summarizes the most typical attacks against SCADA systems, the ways in which they occur, and the tools commonly used. More specific, the following modes of attack are presented.
Read more…
Specially Designed RFID Tags Provide Solutions for Complex Business Needs
BY KEN HORTON
Radio frequency identification technology has been embraced by a growing number of industries to improve the quality and timeliness of data used for asset management. RFID systems collect data automatically, freeing up time, labor and capital resources and reducing costs. Businesses need high read rates from RFID tags to ensure the accuracy of their data. Selecting the right tag—standard or custom—is critical to the proper functionality of an RFID system.
While a standard, off-the-shelf tag works well for many applications, there are circumstances under which a standard tag falls short. When optimizing performance becomes tricky or impossible with a standard tag, it is worth considering a custom tag to improve an RFID system's performance. There are several factors that may make it difficult for a standard tag to meet the requirements of a given business process. Here are some of the most critical factors that might dictate the need for specially designed tags.
Environmental Materials
The materials on which a tag is mounted, the materials surrounding it and any materials that may be moving around the tag during the business process all impact how well a reader will pick up its signals. A tag designed to compensate for or take advantage of these environmental factors can often out-perform a standard tag designed without such considerations.
The factor that most often impacts the performance of RFID systems is the amount of metal in the tag's environment. Tags that will be mounted on or near metal must be properly designed to work on a conductive substrate. Clever engineering can improve the read range of tags mounted on metal or other conductive surfaces.
RFID energy cannot pass through metal, so tags can be missed if they are positioned in the shadow of a nearby metal object. On the other hand, metal reflects some RFID energy, and a tag design can take advantage of these reflected signals. Other materials that can affect tag performance are fluids, both liquid and in the form of high moisture content in wood or other hydrophilic materials. Proper tag design can compensate for these material-related effects and ensure good read rates even in these challenging environments.
Durability
Standard tags are designed for applications that place standard duress on the tag. Most RFID tags are designed for the benign conditions of an office, retail or warehouse setting. They cannot tolerate much exposure to moisture, high heat levels or sub-freezing temperatures. Other tags are designed for outdoor use. They can handle the rigors of exposure to any sort of weather conditions, from the moisture and cold of an arctic expedition to a desert safari.
Yet another level of durability applies to tags that can withstand the extreme conditions of industrial processes like paint-curing chambers, autoclave sterilization or cryogenic storage. If an asset being managed is subject to extreme conditions, a tag tailored to tolerate these conditions will be needed.
Stressors that a custom tag can be designed to tolerate include extremely high or low temperatures, very acidic or basic chemistries, high or low pressures, high vibration and extended immersion in fluids. A medical device manufacturer's analytical product that is subject to high-temperature environments makes a custom tag the right solution to achieve durability. Over-the-road vehicles exposed to road salt and freezing temperatures require another type of durability. There are many applications for which an off-the-shelf tag may not have the right set of durability attributes for a particular use case.
The Right Fit
Another factor that motivates customers to develop special tags is geometric constraints. Some devices have limited space in which to mount a tag, or the space has an unusual shape. In other cases, the tag must fit around or into another device whose geometry is not compatible with the square or rectangular shape of most standard tags. A designed-to-specification tag can often solve tagging problems that are driven by the geometric constraints associated with the item being tagged. For example, doughnut-shaped tags are called for to fit around cylindrical parts. Tags can also be designed to fit into cavities in other parts.
Cost Considerations
Every application has cost constraints, and sometimes a standard tag will not meet those constraints. With a designed-to-purpose tag, it is often possible to strip out the features of a standard tag that are not needed for the customer's application, but which add significant cost.
Features of standard tags that add cost but do not always provide benefit to the user include holes for bolt or screw mounting, a plastic cover or encasement, and an expensive construction material for which another material can be substituted. With a clean sheet of paper, the designer can focus on delivering the RF performance needed by the application without features or materials of construction that are not needed, and can reduce the cost of the solution by providing only the needed feature set.
Engineering for the Application
Developing a specially designed tag starts with clear objectives and requirements, including timeline, cost, geometry and the environment of the business process in which the tag will be used. Once the requirements are clearly understood, the designer can determine whether an existing tag design can be adapted to the use case—an option that is lower-risk, lower-cost and shorter-cycle—or if a completely new design is required. The RF performance of the new design will be modeled and simulated electronically. Then a prototype design will be created, and materials for construction of prototypes will be assembled. Modeling is rarely perfect, so several variations of the tag will be built so the best design for the application can be determined experimentally in the real world.
Tags are tested in standard conditions for baseline performance and then in conditions simulating ways in which they will be used. Through an iterative process, the design that best meets the requirements is selected for use in a pilot run or full production. The process for creating an application-specific tag is more complex and costly than selecting an off-the-shelf tag. However, there are business processes for which standard tags will not work, others in which they provide poor performance and yet others for which they are too costly. Tailored tags can provide benefits in terms of performance, durability and cost, which will result in an RFID system that provides a superior ROI.
Ken Horton is the CEO and cofounder of Vizinex. He focuses his time on sales and marketing and also being the CFO. Ken has worked in the RFID field since 2008, in operations roles as well as in sales and marketing. Prior to the founding of Vizinex, he served in executive positions in several small high-technology firms. His experience includes leadership positions in operations, engineering, and sales and marketing. For 25 years, his industry experience has included medical instruments, automated electronic assembly equipment, PC-related hardware and software products, and semi-conductor production equipment. Ken has an engineering sciences degree from Dartmouth College and an MBA from Stanford University, and he is a graduate of General Electric's two-year Manufacturing Management Program.
The Power of Serialization in Planning, Execution and Risk Aversion
BY ANSHUMAN AGARWAL
Inventory optimization and controlled supply chains are the need of the hour. While COVID-19 revealed supply chain shortcomings at the planning level, for example, the global retail industry witnessed inventory distortion of $1.8 trillion in 2020. There are challenges at the operational level, such as counterfeiting and illegal diversions, that also require immediate attention since they directly impact customers' safety and threaten brand image.
Inventory serialization—tracking individual pieces using unique serial numbers, similar to the international mobile equipment identity (IMEI) specific to a smartphone—is fast becoming a necessity to fight these challenges. From ensuring product delivery to providing waste management and fraud detection, serialization is helping brands attain complete visibility across their supply chains. RFID tags, QR codes and unique piece barcodes (UPBs) capture a product's journey and are used for serialization. They help in decision-making at the granular level and in determining the product's future.
Planning
Demand Planning: Serialization can access locational usage and help resolve demand supply mismatch issues. It can gather real-time data on performance indicators and evaluate the effectiveness of a product or service. It can also suggest improvements so brands can design specifically for the market. Action on emerging needs, trends and changing behavioral patterns can be taken rapidly to boost business. Based on a brand's regional capabilities, purposeful collaborations and partnerships can be made to serve local customers better.
Performance Assessment: Serializing inventory can help companies monitor a product's complete lifecycle, from launch and growth to maturity and decline. Industries dealing in items that present life-safety hazards if defective or expired—such as pharmaceuticals, CPG and so forth—can track each component to assess efficacy and viability. Businesses dealing in trends and fashion products can also use this data to make strategic calls on when to remove a non-performing style, discount a less popular design or capture a growing demand.
Better Inventory Control: Proper tracking and order management help to optimize inventory, shorten replenishment lead times, avoid stockouts and increase cash flow. By distributing inventory per demand, a company can avoid the unnecessary tying up of capital at one location. Items that have a short lifecycle, such as food and beverages, as well as fashion and children's products, can be moved through inter-store transfers within a region, in the shortest amount of time, in order to optimize sales and minimize inventory holding.
Sustainable Practices: The ability to track a product's journey back to its origin can help buyers and sellers ensure the usage of ethical, environmentally friendly practices. Industries such as fashion, which are currently under the radar for causing global environmental damage, can use serialization capability to practice sustainable retailing by measuring inventory accuracy and preventing inventory distortion.
Operations
Track-and-Trace: Serialization enables digital capabilities in physical products and helps to provide 100 percent visibility during the production, distribution and delivery phases. It helps to identify gaps and increase accountability at every stage of the supply chain. Faulty products can be returned to their origin, and issues can be traced to the root to prevent them from happening again. This is of great importance today, as offshore manufacturing gains prominence in most businesses.
Theft Prevention and Anticounterfeiting: Counterfeit products tarnish brand image and hamper revenue. Serialization can prevent high-quality and authentic products from slipping into the hands of unauthorized dealers, into the gray market or illegal channels in a region. Securing robust information on unique serial numbers can red-flag any attempts at cloning or other unusual activity, and immediately notify brands and buyers about fraud detection through alerts and messages, thus discouraging it from happening again.
Recall Management: Inventory reconciliation becomes easy with serialization; hence, product recalls can be faster and more accurate. By narrowing down defaults and defects to the individual product level, a company can take action immediately, reducing costs and negative impact on brand image.
Organized Warehousing: Fully automated, scanned-based operations and tracking at critical stages of inward, picking and packing allow warehouse personnel to dispatch the correct item within a service-level agreement. End-to-end traceability helps to enable faster auditing, cycle counting and bin consolidation within a warehouse. It also allows the "first in, first out" (FIFO) method of inventory control, thereby preventing old stock from becoming lost or misplaced. Unaccounted items can be tracked precisely and mapped to the right location. Since every action about each stock-keeping unit is captured, this helps to address the issue of accountability and improve manpower efficiency.
Supply chains are constantly becoming more complex. It is time to tighten the reins and build a strong foundational framework that is well-monitored and secured. Serialization is the most granular unit of inventory measurement and will form the future of inventory management. It can optimize processes and generate opportunities for new capabilities. As digitalization and technological advancements help us to build a better future, let us work toward the foundation and ensure our back end is secured, too.
2021 RFID Trends for Industries and Events
By RFID Journal
For all of the issues and challenges it brought, we may most will remember- 2020 as the year of the rapid adoption of new technologies under some of the most trying conditions. Businesses around the world who were slow-walking their digital transformation initiatives had to adapt quickly and implement a variety of new solutions to maintain their operations.
One way companies can build enterprise-wide intelligence is using the latest radio frequency identification (RFID) technology. With the market expected to grow at a 9% compound annual growth rate (CAGR) and almost every industry benefiting from the technology, RFID is the ideal solution for any organization that needs greater visibility their supply chain. RFID also found many new applications, helped speed up retail processes, and allowed healthcare workers to track or trace individuals during the pandemic.
Top Seven RFID Trends to Look For in 2021
By providing a completely new way to track people, products, or any other commodity, RFID is no longer an emerging technology. RFID is suitable for use cases in almost any industry, including the healthcare, automotive, aerospace, and retail sectors. Accurately keeping track of inventory, inbound logistics, order fulfillment processes, or your entire supply chain provides clarity and insight into your organization's efficiency. Here are seven areas in which RFID is helping to improve business processes around the world.
Improving Retail Efficiencies
In retail environments, RFID can help improve stock and inventory accuracy while automating many of your company's manual processing tasks. From the receiving dock, shipping and distribution processes, to quickly locating an item in the stores, RFID helps speed up every element in the retail industry. You can even ensure automatic replenishment of inventory with the right solution. RFID implementation is changing the way organizations operate every element of their supply chains for greater visibility and accurate accounting of revenues. In 2021, this trend will continue and may even disrupt regular order fulfillment processes, including final delivery to the end user.
Tracing Traffic Inside the Store or Location
Keeping track of everyone who enters your facility is no longer optional. The COVID-19 pandemic requires businesses around the world to keep track of all the people who enter a location for safety reasons. Implementing a RFID system with accurate tracking for everyone who enters your store or building will ensure you can alert any individuals who encountered an infected person at that location. RFID also allows you to track equipment and products. You can plot the movement of items throughout your store to help you optimize processes based on historical data. The retail use cases for RFID include generating customer and product flows throughout the facility; ensuring you can see employee movements throughout the building; and tracking equipment and the users who accessed them during the workday.
Streamlining Checkout Procedures
Traditional checkout and payment processes are time-consuming and labor-intensive. Automating the procedures can help create a frictionless checkout and payment system. Another application is automating your customer loyalty program by recording all the items in a basket once the customer leaves the store. RFID systems don't depend on scanning every item like with barcode solutions. As the reader can tally the products automatically, you can charge customers and accept payment without any human resources involved in the process.
Reducing Theft and Improving Security
Theft remains a major concern for retailers, cutting into their bottom-line and leaching their profits. To secure every product, you can compare the flow against payment and sales data. Using RFID to track products throughout the facility will provide you with details about when a product left the store, who carried out the theft, and help police identify the perpetrator. You can also set up an exit tracking system that will alert you if someone tries to skip the checkout process, automatically triggering alarms. With an integrated RFID solution that keeps track of every product through your entire process, you can limit losses and prevent theft.
Investigate and Verify Your Supply Chain
More customers now care about the safe, responsible, and sustainable sourcing of raw materials and products. New applications for RFID technology continue to disrupt traditional business processes and provide new insights into the entire supply chain. A survey found that 52% of respondents were using active RFID technologies in some capacity. Monitoring your supply chains from inception to completion will also ensure you identify any issues early and can respond effectively against exploitative practices.
Automatic Vehicle Identification
RFID applications are particularly popular in situations where you need to identify items that move through a specific point automatically. Gathering traffic data for automobiles or keeping track of border entries and exits are easier with an RFID system. Electronic toll collections, tracking volumes of cars using a particular road, and monitoring the service history of cars are all new use cases where RFID proved to be invaluable. Creating an electronic record of an automobile's history and traveling patterns can help city planners, federal agencies, and retailers equally well.
Event Management and Safety
Although many in-person events will no longer go ahead during the pandemic, organizers can use RFID to improve conference safety and comply with all applicable regulations. Keeping track of attendees, their movements, and amount of people inside the facility at any time ensures organizers can manage how many people enter a venue, oversee their movements during the conference, and grant access to specific areas or sessions easily. Combining RFID with intelligent Internet of Things (IoT) sensors provides a safer, controlled event that reduces risk and ensures you can contact-trace attendees.
Discover the latest 2021 RFID trends at RFID Journal LIVE!. At LIVE!, we help organizations create unique experiences bringing together innovators who are at the edge of identification, tracking, and monitoring technologies. With 2021 looming, the main trends will be solutions that let you know who visited your locations, what they interacted with, and who else was there to keep your staff and consumers safe. To see where we can meet up at the next event, check out this page.
Health Frontiers: How RFID Helps Control and Prevent Infections and Medical Errors
By RFID Journal
The medical sciences are always looking for ways to implement innovative approaches to healthcare infrastructure, supply chains, and operational workflows. Recently, this drive toward digitalization and technology adoption became a priority for governments, regulatory bodies, and private organizations alike. It's because deploying technologies like RFID in healthcare can have an immediate impact on the entire process.
Five Benefits of RFID in Healthcare Systems and Infrastructure
In the medical and healthcare industries, RFID can assist wherever there is a need to manage, track, control, or stage resources. In pharmacies, RFID is helping to track medicine distribution from the manufacturer to the patient fulfilling a prescription. Medication managers throughout the manufacturing, distribution, and delivery stages are looking to RFID for improving control and limiting access to controlled substances.
The technology behind RFID and Near Field Communication (NFC) enables labs, hospitals, and the entire medical supply chain to track and trace biological samples, equipment, and drugs throughout their daily processes. With additional scrutiny required on drug and preventative medicine distribution and delivery, RFID is uniquely suited to overcome all these challenges. Here are some of the key areas in which RFID is making a positive impact on the prevention of infections and medical errors.
Reducing Medical Errors
Every year, thousands of patients die in hospitals and healthcare facilities due to medical errors. With the complexity involved in providing adequate care to patients, it's easy for a mistake to creep in when physicians do not have access to accurate patient information. According to some estimates, the number of patients who succumb to medical mistakes every year can be as much as 195,000. With RFID systems, healthcare providers can help prevent many of these errors and save lives. Clinicians, doctors, and emergency medical personnel need access to accurate and up-to-date information when responding to events. RFID enables the storage and rapid access to data using unique IDs that provide all the relevant incident data and medical history. With quick access to all relevant patient information, everyone from crisis management teams to emergency responders can ensure they provide the correct treatment and reduce the risk of a fatal error.
Enhancing Patient Care and Surgical Procedures
A range of different RFID healthcare applications has enabled medical practitioners to streamline everything from patient intake to traumatic events. RFID applications for patient care and surgical procedures include optimized billing and invoicing, since suppliers of components, devices, and consumables use RFID to generate accurate invoices automatically for procedures; improved patient safety, since companies use RFID to track consumables in surgeries, such as sponges, to make sure they didn't leave anything behind after the procedure; accurate patient identification, since RFID tags are helping physicians to accurately identify patients and prevent wrong-site or wrong-procedure occurrences in hospitals; and post-procedure monitoring, since after a procedure, monitoring the patient's vitals is possible with RFID tags that have capabilities like measuring temperatures or recording falls. RFID also makes it possible to increase operational efficiencies in hospitals by tracking administrative processes, managing throughput times effectively, and optimizing room utilization. With increased visibility into all healthcare operations, RFID allows administrators to pinpoint different areas where it's possible to improve.
Managing Disease Outbreaks and Pandemics
During pandemics (or during outbreaks that could lead to pandemics), RFID systems can track and trace patients, caregivers, and the vaccination process. For caregivers, facilities must track all movements to determine exposure. With vaccines, every dose may need special care during transportation and distribution to ensure its efficacy when being administered. RFID solutions can span the entire manufacturing, distribution, and administration process from start to finish. Serializing products with RFID tags, including real-time location systems (RTLS) in the procedures, and managing stock levels in times of crisis are vital in preventing an outbreak from becoming another pandemic.
Improving Hygiene Practices in Hospitals and Care Facilities
Hand-hygiene compliance is another area in which RFID systems can assist. Real-time continuous monitoring and tracking of all hand-hygiene practices prevent a healthcare worker from spreading a disease to other patients. Usually, an observer carries out all compliance checks, but this is intermittent and delivers inconsistent results. The subject will know the person is watching them for a set period. RFID location tracking gives compliance officers the ability to track the complete path of every caregiver and monitor (or record) all hand-hygiene events. In one case, RFID system tracking combined with CCTV footage had an accuracy rate of 93% compared to in-person observations. When dealing with an infectious disease, ensuring everyone remains compliant with the medical facility's procedures and rules remains a primary concern for everyone involved in the healthcare industry. RFID makes these oversight and governance processes easier to deal with and provides teams with accurate results.
Capturing and Generating Statistical Data
Administrators need accurate data that covers the entire medical and healthcare provision process to make informed decisions about resourcing, equipment inventory, and consumable consumption. Accurate information about all the elements required to improve the level of care in facilities using RFID-enabled middleware can optimize almost every portion of the process. Administrators can track staff during their shifts, count the medical machines in their inventory, record servicing and maintenance activities on devices, and monitor drug-delivery processes. This information helps planners and decision-makers to reduce bottlenecks and ensure the timely resupply of key consumables without requiring manual stock counts. Accurate location, procedure, and inventory data give administrators clear insights into their current procedures and, more importantly, generate precise data that informs all future decisions.
For more RFID in healthcare applications, join us at RFID Journal LIVE!. RFID and NFC systems are reshaping the world's medical supply chains, healthcare quality, and drug delivery systems. To find out more about the latest applications and use cases, join us in September 2021 to see what new capabilities RFID has to offer. We are also hosting digital events during the year, so check back regularly to find a track that applies to your organization or industry.
AIM Global Updates RFID Testing Standard for Medical Devices
BY CLAIRE SWEDBERG
The latest version of the 7351731 standard offers updated guidance to help medical device manufacturers and users test their products with UHF, HF and LF RFID readers, to ensure immunity to RF transmission effects.
Industry standards group AIM Global has released the latest version of its standard for the testing of non-implantable wireless medical devices, to help users and manufacturers better determine if they are immune to emission from RFID technology. AIM's 7351731 standard provides companies with guidance to test medical devices and determine whether RFID transmissions pose any risk to their operability. The standard offers test protocols for 125 kHz LF and 13.56 MHz HF RFID compliant with ISO 15693, as well as UHF RFID transmissions and both active and passive technologies.
AIM is a global industry association that offers networking, education and advocacy to promote and standardize automatic-identification technologies. It covers RFID, barcoding and smart devices used in Internet of Things (IoT), real-time location system (RTLS) and blockchain applications. The organization's latest healthcare standard revision, which it announced in June of this year, provides updates to the previous version of the standard, which was developed by AIM's healthcare initiative workgroup, within the RFID Experts Group (REG HCI), according to Mary Lou Bosco, the COO of AIM and AIM North America.
Mary Lou Bosco
RFID is frequently used in healthcare environments for asset and inventory management, as well as for patient and personnel tracking. For instance, RFID tags can be applied to high-value equipment, laptops, carts and medications, as well as to packaging for surgical implants and tools. RFID-enabled wristbands and badges can be worn by hospital personnel, in addition to both adult and infant patients.
Test labs have been testing against the standard for several years, Bosco reports, and some have provided suggestions for improving the testing protocols to the AIM working group. This third version of the standard is intended to reflect the latest testing needs, and to be easier to implement than previous iterations. The update is part of regular review and revisions that AIM provides for all of its standards, "AIM periodically reviews these documents," Bosco states, "to make sure all the information is up to date and conforms with the most recent technology advancements."
Several ISO/IEC documents have been revised since the release of the initial standard, and AIM thus updated its standard to accommodate those changes. The working group adjusted the standard according to requests from RFID solution designers, Bosco says, as well as from medical facility engineers and administrators. All of the previous groups have performed the test methods and test levels for evaluating the electromagnetic immunity of non-implantable medical electrical equipment and systems to electromagnetic emissions from RFID readers. AIM has been working with these parties, she says, "to give as clear guidelines as possible with how to perform the testing."
The changes, which include clarification of some figures to make them easier to interpret, take into account updates to several ISO/IEC documents, as well as comments from the labs that performed the testing in the standard. "The specially appointed workgroup thought that enough new information was available to update the standard," Bosco says, "and make testing methodologies clearer for those reading and implementing the standard."
The standard guides medical device manufactures and end users on how to evaluate their devices' immunity to emissions as RFID readers interrogate tags within the vicinity. The test procedures are based on experimental results from several AIM members and testing labs that performed the standard's test methods, Bosco says. Working together, these parties reached an agreement on how testing should be performed and the verbiage that should be used to specify the standard's testing requirements.
Test protocols are included for the major commercial implementations of RFID. The standard is designed for testing existing medical electrical equipment and systems. For the purposes of this standard, Bosco notes, other technologies, such as Wi-Fi and ultra-wideband, are not considered. Instead, she says, LF, HF and UHF represent the most common RFID technologies currently deployed in healthcare environments.
While there is no official certification process for devices that pass testing, AIM has encouraged those that have carried out testing to contact the association with their results so that it may continue to collect a list of those who claim they can perform the test. The standard guidelines can also offer guidance for RFID solution designers, to help them determine during the designing stage whether medical electrical equipment and an RFID solution environment are compatible. Immunity to RFID reader testing is required by the FDA for medical devices.
According to the FDA, the use of RF wireless technology offers advances in healthcare, but because airways are shared, the function of a wireless medical device could be affected by the presence of other wireless devices within the vicinity. One example might be losing data or experiencing disruption in operation. The FDA advises healthcare facilities to consider the selection of wireless technology, quality of service, coexistence and security when choosing RFID and other wireless technologies.